A substance that is found in fruits and vegetables from
berries to cucumbers stop memory loss that comes with Alzheimer's illness in
rats, scientists have found. In tests on rats that normally develop Alzheimer's
illness signs less than a year afterbirth, an everyday dose of the substance --
a flavonol known as fisetin -- avoided the progressive memory and studying
problems. The medication, however, did not change forming amyloid plaques in
the brain, collections of necessary proteins, which are generally held
responsible for Alzheimer's illness.
A substance that is found in fruits and vegetables from
berries to cucumbers stop memory loss that comes with Alzheimer's illness in
rats, scientists at the Salk Institute for Biological Research have found. In
tests on rats that normally create Alzheimer's illness signs less than a season
afterbirth, an everyday amount of the substance -- -a flavonol known as
fisetin
-- -prevented the modern storage and studying problems. The medication,
however, did not change developing amyloid plaques in the mind, collections of
necessary proteins, which are generally held responsible for Alzheimer's
illness. The new finding shows a way to cure Alzheimer's illness symptoms
individually of focusing on amyloid plaques.

"We had already
shown that in normal animals, fisetin can improve memory," says Pamela
Maher, a senior staff researcher in Salk's Cellular Neurobiology Laboratory who
led the new study. "What we revealed
here is that it also can have an effect on animals vulnerable to Alzheimer's
illness."
More than a several years ago, Maher found that fisetin
helps secure nerves in the mind from the results of getting older. She and her
colleagues have since -- -in both separated cell cultures and mouse studies --
-probed how the substance has both antioxidant and anti-inflammatory results on
cells in the brain. Most recently, they found that fisetin changes on a
cellular pathway known to be engaged in memory.
"What we noticed
is that fisetin has various qualities that we thought might be helpful when it
comes to Alzheimer's illness," says Maher.
Parents are advised to make sure their kids drink milk and eat other calcium-rich foods to build strong bones. Soon, they also may be urged to make sure their kids eat salmon, almonds and other meals high in nutrient magnesium -- another nutrient that may play an essential part in bone health, according to a researched presented Sunday, May 5, at the Pediatric Academic Societies (PAS) annual meeting in Washington, DC.
"Many nutrients are key for kids to have healthy and balanced bone fragments. One of these is nutrient magnesium," said lead author Steven A. Abrams MD, FAAP, professor of pediatrics at Baylor College of Medicine in Houston. "Calcium is essential, but, except for those kids and adolescents with low intakes, may not be more essential than nutrient magnesium."

While it is known that nutrient magnesium is essential for bone health in adults, few studies have looked at whether nutrient magnesium consumption and absorption are related to bone nutrient material in youngsters. This research aimed to fill that gap.
Researchers recruited 63 healthy and balanced kids’ ages 4 to 8 years old who were not taking any multivitamins or nutrients to join in the research. Children were put in the hospital overnight twice so their magnesium and calcium nutrient levels could be calculated.
Breast feeding and small amount of solid food after the 17th week of birth could reduce meals allergic reactions in babies, according to University of Southampton analysis.
The analysis, led by Dr. Kate Grimshaw, dietitian and senior analysis colleague at the University, say that giving the baby solid food besides breast-feeding helps it create a better, stronger defense mechanisms to fight food allergic reactions.
"Introducing solid foods alongside breast-feeding can benefit the defense mechanisms," Dr.Grimshaw explains. "It appears the defense mechanisms become educated when there is an overlap of solid foods and breasts milk because the milk promotes tolerogenic mechanisms against the solids."
 "Also, our results suggest 17 several weeks is an important time point, with solid meals introduction before now appearing to advertise allergic disease whereas solid meals introduction after that period time point a promote tolerance."
"Also, our results suggest 17 several weeks is an important time point, with solid meals introduction before now appearing to advertise allergic disease whereas solid meals introduction after that period time point a promote tolerance."
Infants are largely intolerant of solid meals before four to six months of age. This is thought to be because of the infant gut being immature, which may cause symptoms of meals allergic reaction.
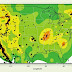
The number of earthquakes has changed over the past several years within central and eastern United States. Nearly 450 earthquakes scale 3.0 and higher happened in the four years from 2010-2013, an average of over 100 each year, compared with an average rate of 20 earthquakes each year noticed from 1970-2000.
Seismicity of the coterminous United States and surrounding areas, 2009–2012. Black spots represent earthquakes with a magnitude ≥ 3.0 are shown; bigger spots represent events with a magnitude ≥ 4.0. Background colors show earthquake threat levels from the US National Seismic Hazard Map (NSHM).
 |
Credit:USGS
|
This changed magnitude in earthquakes reminds two important questions: Are they natural, or human induced earthquake? In addition, what should be done in the future as we deal with the causes and effects of these actions to decrease associated risks? USGS researchers have been examining the changes in earthquakes as well as the likely causes, and they have some answers.
Mini ice age is on the way? Scientists let know the Sun has ‘gone to sleep’ and say, it could because temperature ranges to plunge. 2013 was due to be season of the ‘solar maximum’. Researchers say solar power is at a portion of what they expect.

The Mini Ice Age is a period between about 1300 and 1870 during which European countries and
North America were exposed to much chillier winter seasons than during the 20
th century. The period can be separated in two stages, the first starting around 1300, and recurring until the late 1400s. There was a little bit hotter interval in the 1500s, after which the environment worsened. The interval between 1600 and 1800 represents the height of the Mini Ice Age. Developing European trade and developing European sea, born Empire has classified the interval. This was straight connected to developments in technological innovation using more of nature’s power and towards the end of the interval fossil-fueled power. These two hundred years also saw the expertise of farming areas, which produced particular products for regional and worldwide market.
Cancer is an illness that creates worry, so it is not surprising the community is desperate to recognize ways to reduce the threat. The media often features details on "Miracle Foods" and publicizes whether these meals can reduce the chance of cancer.
"Reality Check: There is No Such Thing as a Miracle Food," released in Volume 65, Issue 2, 2013 of Nutrition and Cancer: A Worldwide Publication, is a comments published by the University of Minnesota's Maki Inoue-Choi, Sarah Oppeneer, and Kim Robien that phone calls on both scientists as well as media to consider the credibility of several research in contrast to unique research before supposing that media details is actual.
 "Nutritional scientists and epidemiologists should be aware of the community health information that are taken away from their individual research and not sensationalize the results or promote the press craze around a single study," the writers believe.
"Nutritional scientists and epidemiologists should be aware of the community health information that are taken away from their individual research and not sensationalize the results or promote the press craze around a single study," the writers believe.
The writers discuss two individual research that imagine a reduced chance of ovarian cancer because of falconoid in red onion and omega-3 in sea fish. Both of this research was revealed as facts on a popular TV discuss show. The writers claim that with further research, three other researches would have been found that could disprove the results revealed as true.
"The community needs more details about the effect of diet as a whole on cancer threat, as well as the significance of doing and keeping an ideal bodyweight, frequent exercising, and preventing an inactive way of life," the writers said.
There is an application that can read your mind via your mobile device. The technological innovation is known as predictive analytics, and Google’s Now app is at the top edge. Other applications that carry out predictive analysis include Grokr and Osito: forecasting the smart phone user’s next move.
How does this work?
An algorithm, resulting in a forecast of the user’s next actions, builds snippets of details.
An example would be mixing snippets of calendar records with the user's place information, email details, online community posts and other like details.
 The user is then provided with support the application “thinks” is needed. The support-information is known as a card. A card might, for example, remind the user about a meeting whose details was joined formerly.
The user is then provided with support the application “thinks” is needed. The support-information is known as a card. A card might, for example, remind the user about a meeting whose details was joined formerly.
The application will then add guidelines to the occasion or show varying climate circumstances at the location—even recommend raingear.
Benefits
- The Google Now application can “understand” perspective and narrow out unrelated details, making searchers easier than ever.
- The Google search engine can now react to more than just individual search phrases and can clearly understand the importance of a search for question. This algorithm is known as Hummingbird and 90 percent queries impact.
An example is that Google can evaluate items on demand or dig up information about various things. For example, just type in the name of a popular landmark—once. If you look for trivia, you will get solutions, but if you then look for directions, Google will know that you want guidelines to this landmark without you having to type in its name again.
- Future locations of the user can be predicted (based on places visited previously), not just the current place.
- Recently, Google and Microsoft researchers came up with software, Far Out, that can find out a user's schedule by means of GPS monitoring. This information is then formed so upcoming places of that user’s can be predicted.
- The configuring can even adjust to link with the user's changes in property or office.
As innovative as all of this seems, this is only the start of a new trend of technological innovation that can “think” for us—a big benefit to those whose lifestyles are so stressful that they have become absentminded, and for those who simply enjoy the idea of having to do less mental work.
What would you do if you checked your financial bank account and saw a $0 balance? Identity theft is not too unusual of an incident these days, yet we often fall into the snare of thinking that it will always occur to “someone else”. Unfortunately, we are all somebody else’s “someone else”, which means identity theft can occur to you.
Your identity can be stolen in many ways. Criminals can grab your credit cards numbers when you buy on the Internet. They can also steal your identity through hackers, malware, and viruses. They can even manage you into providing up your private information without you even understanding that you are doing it.
 Identity theft is like cancer. If you capture it beginning enough then you can lessen most of the destruction, but if you neglect the signs until its too late then your life just might be broken. Do not let it occur to you. Be on the lookout for these signs to best secure your money.
Identity theft is like cancer. If you capture it beginning enough then you can lessen most of the destruction, but if you neglect the signs until its too late then your life just might be broken. Do not let it occur to you. Be on the lookout for these signs to best secure your money.
1: Unexplained Charges
If you ever have unexplained expenses on your credit or debit cards, that should be an immediate red flag. Does it mean that your identity has been stolen? No. It is possible, for example, that someone wrongly joined in their own credit cards number somewhere, and the resulting number occurred to be yours.
However, an unexplained cost points to fake action. Even if the cost is only for a few dollars, you should always follow up with an unusual purchase and find out where it came from. Some identity thieves will “test” credit credit cards with a few simple buys before going on an exercise. Do not delay until it is too delayed.
Call client support and they should be able to help you find out whether there is dubious action going on or if it was just an error.
Sodium bicarbonate, better known as ordinary baking soda, has been used for decades as a first line of protection against every ‘acidic’ wellness – including cancer. Normally, the question is still – is there any proof that ordinary baking soda is a protection against cancer or any other serious disease?
History has much to teach us about organic medical care. In a brochure named, Arm & Hammer Baking Soda Medical Uses – released in 1924, Dr. Volney S. Cheney explains his medical achievements in using sodium bicarbonate to cure both the common cold and flu. His comments are remarkable…
“In 1918 and 1919 while fighting the ‘flu’ with the U. S. Public Health Service it was brought to my attention that rarely anyone who had been thoroughly alkalinized with bicarbonate of soda shortened the illness, and those who did contract it, if alkalinized early, would almost have mild attacks.”
 Sodium bicarbonate has been and still is used to create the urine less acid. This helps the kidney get rid of the crystals and is used clinically to avoid gouty arthritis and kidney stones. Even athletes use sodium bicarbonate to improve stamina. cells that have enough bicarbonate consume more energy at rest – so they are better able to transport sugar and lactate.
Sodium bicarbonate has been and still is used to create the urine less acid. This helps the kidney get rid of the crystals and is used clinically to avoid gouty arthritis and kidney stones. Even athletes use sodium bicarbonate to improve stamina. cells that have enough bicarbonate consume more energy at rest – so they are better able to transport sugar and lactate.
Can ordinary baking soda help cancer sufferers cure naturally?
Dr. Mark Pagel, of the University of Arizona Cancer Center, is going to use a $2 million grant from the National Institutes of Health to research the potency of ordinary baking soda as a cure to breasts cancers.
This is a medical trial on the use of oral ordinary baking soda for breasts cancers. The grand was granted because of the cancer research that Dr. Robert J. Gilles and co-workers have already successfully showed with the pretreatment of rats – using ordinary baking soda – to alkalize the area around cancer tumors.
They have proven that sodium bicarbonate improves growth pH, stops natural metastases, and decreases the rate of lymph node participation in rats with breasts cancers. In addition, the news gets even better…
Baking soda has been proven to reduce malignancies; cure the acid-alkaline axis by controlling the pH of cells and tissues and improves cell voltage.
By increasing oxygenation – ordinary cooking baking soda stops cells from turning cancer and return dangerous cells to a proper and balanced state. Sodium bicarbonate has been recommended for weak cancer patients. In a few days of therapy with sodium bicarbonate, the cells in the muscles perform better.
More than 2.5 thousand men yearly have a prostate check and listen to bad news. While not all prostate circumstances will become full-blown cancer, it is not an illness you want to create home about, and it can intervene in a person's total well-being. One age-old natural herb once used by the Seminole Indians just might treat an increased prostate though.
 Specifically in the focus where this particular natural herb is involved in a situation called Benign Prostatic Hyperplasia (BPH). While the natural herb has been used for hundreds of years to help men with prostate issues and both genders deal with kidney system issues, all of an unexpected a few research have stated it does not work. Not so fast – Merck & Pfizer, if we have a nearer look at the research in question we can see how Big Pharmaceutical has unique another web of false information to mix up the public about this helpful natural herb.
Specifically in the focus where this particular natural herb is involved in a situation called Benign Prostatic Hyperplasia (BPH). While the natural herb has been used for hundreds of years to help men with prostate issues and both genders deal with kidney system issues, all of an unexpected a few research have stated it does not work. Not so fast – Merck & Pfizer, if we have a nearer look at the research in question we can see how Big Pharmaceutical has unique another web of false information to mix up the public about this helpful natural herb.
BPH is triggered when the prostate’s epithelial tissues and stromal tissues are too high. This causes the prostate to expand, putting stress on the urethra, the passage for pee. This stress can cause great pain when it comes a chance to gap the kidney, and with pain, there is sometimes a loss of overall circulation and therefore a more regular feeling of needing to pee since the body still needs to remove poisons even when BPH is present.
Web services provider Yahoo declared that its email connections are now encrypted by default.Starting now, all access to Yahoo Mail will be encrypted. Jeff Bonforte, the company's senior vice president of communications products said, “We are using Transport Layer Security (TLS)/Secure Sockets Layer (SSL) with 2048 bit digital certificates."
"Yahoo Mail Standard email protocols such as IMAPv4, POP3 and SMTP will be encrypted. The security will apply to the web and mobile interfaces, protecting message content, attachments, calendar items, and contacts. Mobile applications will also be encrypted," Bonforte said.
 The encryption program was announced in October last year. Following revelations by former United States National Security Agency (NSA) contractor Edward Snowden, government spies was in fact tapping network communications between Google, Yahoo, and other web providers' data centers.
The encryption program was announced in October last year. Following revelations by former United States National Security Agency (NSA) contractor Edward Snowden, government spies was in fact tapping network communications between Google, Yahoo, and other web providers' data centers.
Responding to the spy agency's interception of data center links, Google started encrypting all internal networks in November last year to halt the large-scale wiretapping.
Microsoft will stop supporting Windows XP on April 8, 2014. End of support shows Microsoft Company will no more offer any technical support to companies or customers for Windows XP problems.
Even though Windows XP was released way in 2001, it is still an excellent operating system. It is stable, has a Start key and gets the job done. That is why there are many incredible number of computer systems that still have it set up. It is so popular, in fact, it is the second most operating system set up in the world, only a little bit behind Microsoft’s Windows 7 OS.
 Unfortunately, this is not an excellent reason. The purpose until now has been extending the due period for when it would drop support for Windows XP, but now it seems they are going to kill it off. Microsoft will quit aiding Windows XP on April 8 2014. This is big information because it points out in about 4 months; there will be an incredible number of computer that are going to be vulnerable to hackers.
Unfortunately, this is not an excellent reason. The purpose until now has been extending the due period for when it would drop support for Windows XP, but now it seems they are going to kill it off. Microsoft will quit aiding Windows XP on April 8 2014. This is big information because it points out in about 4 months; there will be an incredible number of computer that are going to be vulnerable to hackers.
End of support shows Microsoft Company will no more offer any technical support to companies or customers for Windows XP problems. Besides and most importantly, Microsoft Company will no longer offer any protection patches or updates for the operating system. On top of that, you will not even be able to get Microsoft Security Essentials for Windows XP, the free antivirus application, after this date.
Over 60,000 exposed control systems found online. Researchers have found weaknesses in industrial control systems they say give complete control of systems running energy, chemical and transport systems.
Russian researchers whom throughout the last year probed popular and high-end ICS as well as Supervisory Control And Data Acquisition (SCADA) systems discovered the vulnerabilities. It used to overpower everything from home solar panel installations to critical national infrastructure.

Positive Research chief technology officer Sergey Gordeychik and consultant Gleb Gritsai detailed vulnerabilities in Siemens WinCC software. The elaborated weaknesses were used in industrial control systems including
Iran's Natanz nuclear plant that was targeted by the US Stuxnet program.
Gordeychik said, "We do not have big experience in nuclear industry, but for energy, oil and gas, chemical and transport, we showed to owners how to get full control of industrial infrastructure with all the attendant risks." The vulnerabilities been around in the way passwords were encrypted and stored in the software's Project database and let attackers to gain complete access to Programmable Logic Controllers (PLCs) using attacks referred to as dangerous and easy to launch.
Although many people would not give their phone number to an unknown person on the road, they are contented to share their numbers with Facebook, Google, and added sites. However, as millions of immature Snapchat users simply educated, phone numbers are helpful information to hackers.
On Wednesday, Snapchat happened to be the first corporation to have its important information hacked in 2014. Almost 5 million account consumer names and partial phone numbers were sent online as a forewarning to those making use of the photograph messaging service.
“Our inspiration behind the publication was to raise the public awareness about the issue, as well as put public strain on Snapchat to get this develop fixed,” the suspected hackers told tech site TheVerge.com . The spokesperson for Snapchat refused to comment, although the company unconfined a blog post saying its supplementary counteractions
“to fight abuse and spam.”

Consumers are meant to be cagey about sharing their phone numbers, security experts say.
“Phone contacts are unique identifiers that lean to last for an extended time,” utters Michael Fertik, CEO at Reputation.com, and a site that helps consumers protecting their privacy online.
“You change your phone number a lot less often than your IP address as well as probably even your residential address” when Snapchat users have fake user names. Many citizens use the equivalent I.D. across various social networks, states Graham Cluley, a
U.K. safety blogger and technology counselor.
“Use a different user I.D. than the one you makes use of publicly on Facebook as well as Twitter,” he says. What is added, typing just a cell phone number to the Facebook will expose the profiles of the owner if they added it to their account data.
Out of the 2,736 children who went missing in Karachi last year, FIRs of only 173 were
registered at different police stations, as mentioned in an annual report on
missing children by a nongovernmental organization.
"If a child (under 18) goes out of contact with family or guardians, he
or she is considered as a missing child," said Muhammad Ali, head of
Roshni Helpline, quoting the meaning of a missing child from the Sindh Child
Protection Act, 2013 and the United Nation's Convention on Child Rights
(UNCRC).

Based on the civil society group, about 2,736 children went missing within
the jurisdictions of 114 police stations in the city in 2013. The police
recorded 984 complaints but had included 811 of them as no cognizable cases and
later registered FIRs of only 173 missing children.
Ali mentioned the data in the report was also gathered from mosques as the
"law enforcement did not record every case that being brought to
them."
The nutrients and vitamins that we get from our food are just absorbed when interacting with other nutrients. It works slightly like the engine of a car. For that engine to run, fuel alone is certainly not enough. The nutrients we need should be presented in a manner that encourages several of them as possible to work together.
However, will there be more in getting a healthy diet than taking in natural organic foods? We feel strongly that we are what we eat or more accurately, we are what we absorb.

Take for example carrots, which are best eaten, raw to reduce nutrient loss. Carrots are a great source of antioxidants, Beta-Carotene, vitamins K and C. While carrots can be a healthy option, getting the full benefits of the nutrients you should also eat nuts to supply fats carotenoid and vitamin K absorption. Pine nuts or sunflower seeds claim to be an ideal choice as they have vitamin E, which works synergistically with vitamin C and can be spread over a salad containing raw carrots.
Here are some other examples of foods, which work well together.
Social network beast Facebook is now being charged in California by two consumers who declare the corporation intercepts “substance of …users’ communications.”

According to the class action court case, started by Matthew Campbell and Michael Hurley, Facebook has allegedly driven against the Electronic Communications Privacy Act as well as many
California state laws.
The basis of the pretenders’ grievance is that Facebook’s use of the phrase
“private” is ambiguous when applied to its individual internal messaging program.
Campbell besides Hurley claims the corporation scans confidential messages to be aware of any URLs contained by them. The plaintiffs’ further assert the business follows links that it discovers as part of the swarming procedure, which it has not clearly disclosed to consumers of its service.
New research by IHS Automotive states that by 2025, a mere 11 years from now, there will be 230,000 self-driving cars on earth's roadways. By 2035, 9.2-percent of new cars sold will likely self-directed, as costs are driven down to only $3,000 more than a traditionally controlled car.

We are probably to be obsolete soon. Ten years beyond the predicted date, the number will puff up to 11.8 million, although exclusive select models will do without having any traditional means of human control through 2030. By the middle of the 21st century, almost every car on the road will likely be of the self-directed variety.
This may only be a study for now, but it is the one that we think might hold some water. Several traditional manufacturers are getting into autonomous-vehicle projects, and they are being joined by players like tech giant Google with many major industry manufacturers.
Two Internet security companies have stated that Yahoo's advertising and marketing servers were spreading malware to several a huge numbers of users during the last few days. The attack is the work of malicious people whom have stolen Yahoo's advertising network for their ends.
Fox IT, a security company found in the
Netherlands, published a blog post on Friday explaining the problem.
"Clients browsing Yahoo.com received advertisements served by ads.yahoo.com. A few of the advertisements be malicious," the company reported. Rather than providing ordinary advertisements, the Yahoo's servers reportedly forward users an
"exploit kit" that
"exploits vulnerabilities in Java and installs a host of various malware."

Ashkan Soltani, a security researcher and Washington Post contributor, alerted me to the issue. Often, he says, these attacks are
"the results of hacking an existing advertisement network. However, there is another possibility," he says. The offenders may have merely sent the harmful software as ordinary advertisements, coming past Yahoo's system for removing malicious submissions.
Phil Everly, who with his brother, Don, comprised the most venerable vocal duet of the rock and roll era. Their elegant musical harmony deeply shaping the Beatles, the Beachboys, the Byrds and countless younger-generation rock. Folk and country vocalists, passed away Friday in Burbank, California of complications from prolonged hindering pneumonic disease, his wife, Patti Everly, told the Los Angeles Times.
He was 74. “We are brokenhearted,” she said, mentioning the disease comprised the result of a lifetime of cigarette smoking. “He struggled long and backbreaking.
 ”On the height of their popularity in the late 1950s and early 1960s, the Everly Brothers charted almost three dozen hits on the Billboard Hot 100 singles chart. Among them “Cathy’s Clown,” “Wake up Little Susie,” “Bye-Bye Love,” “When Will I Be Loved” and “All I Have to Do Is Dream.” The Everly Brothers were one of the first 10 performers inducted into the rock music hall of Fame when it took off in 1986.zoom
”On the height of their popularity in the late 1950s and early 1960s, the Everly Brothers charted almost three dozen hits on the Billboard Hot 100 singles chart. Among them “Cathy’s Clown,” “Wake up Little Susie,” “Bye-Bye Love,” “When Will I Be Loved” and “All I Have to Do Is Dream.” The Everly Brothers were one of the first 10 performers inducted into the rock music hall of Fame when it took off in 1986.zoom
“They had that sibling sound,” said Linda Ronstadt, who marked among the greatest hits of her career in 1975 with her recording of “When Will I Be Loved,” which Phil Everly wrote. “The information of your DNA is carried in your voice, and you can get a sound (with family) that you never get with somebody who has not akin to you. In addition, they were some such good singers-they were among the foundations, one of the cornerstones of the new rock ‘n’ roll sound.
”Robert Santelli, executive director of the Grammy Museum in Los Angeles, said Friday, “When you talk of musical harmony singing in the popular music of the postwar period, the first target you get is the Everly Brothers. ... You might link between all the 1950s outstanding doo-wop groups and what would come out the 1960s with the Beachboys and the Beatles. They showed up the Beach boys and the Beatles how to sing harmoniousness and integrate that into a pop music form that was irresistible.
”Besides his wife, his brother, Don, their mother, Margaret, sons Jason and Chris, and two granddaughters, survives Everly.
An ingredient traced from traditional Chinese natural treatments has been found good at relieving pain. Aiming the way to a different no addictive analgesic for chronic inflammatory and nerve pain, according to UC Irvine pharmacological medicine researchers.
Working with Chinese scientists, Olivier Civelli and his UC Irvine co-workers separated a compound called Dehydrocorybulbine (DHCB) from the roots of the Corydalis yanhusuo plant.
In tests on mice, DHCB turned out to reduce both inflammatory pain, which is associated with damaged tissues and the infiltration of immune cells, and damage-induced neuropathic pain, which is a result of injury to the nervous system. This will be significant because there are no current enough treatments for neuropathic pain.
 |
Corydalis yanhusuo plants
Credit: herbalextractok |
However, the study found that DHCB did not produce the threshold seen with continuing use of most conventional pain cures, such as morphine.
“Nowadays the pharmaceutical industry battles to find new medicines. Yet for centuries, people have applied herbal treatments to address variety health problems, including pain. The purpose was to find out substances in these herbal cures that may help us discover new ways to treat health conditions,” said Civelli, the Eric L. & Lila D. Nelson Chair in Neuropharmacology. “We’re enthusiastic this one shows promise as an effective pharmaceutical. It also shows a different way to understand the pain process.”
Most Americans know the U.S. economy is seriously dependent on consumer spending. If typical Americans are not out there spending money, the economy is likely not to do well. Regretfully, retail selling during the holiday season is disappointing and the middle class consistently seriously struggle. Families are going to have less money in their pockets to spend because of much increased health insurance premiums under Obamacare.
Unfortunately, for them, millions of those families were hit with massive health insurance rate increases.
Health insurance premiums for men are likely to go up by an estimate of 99 percent under Obamacare and health insurance premiums for women will go up by an average of 62 percent under Obamacare.
Most middle class families simply cannot afford that.

Millions of families are receiving letters just like that. In addition, to say that such rate increases are a "surprise" to most people would be a massive understatement. Even people that work in the financial industry are shocked at how high these premiums are turning out to be...
"The true big surprise was how much out-of-pocket would be needed for our family," said David Winebrenner, 46, a financial adviser in Lebanon, Ky., whose deductible topped $12,000 for a family of six for a silver plan he was considering. The monthly premium: $1,400.
Since Americans are going to have to pay much more for health insurance, that is going to remove a huge amount of discretionary spending from the economy, which will not good news for retailers.
The two Jamaicans happened to be out fishing on a Sunday morning (November 2013) when they hooked what ended to be a 900-pound scale less beast of a fish. Both fishers, Desmond Phillips and Michael Grant, had never seen anything that looked like their strange, midmorning catch and at one point were frightened that they had someway captured an alien.

The monstrous fish was later identified as a
“sunfish”. Not a native inhabitant of the waters along the coast of
Bryans Bay in
Portland, Jamaica. The sunfish consumes mostly jellyfish; however has a taste for squids, sponges, Portuguese man of war and other various invertebrates.
The Ocean Sunfish (Mola or Mola Mola) is a slow-moving fish that likes to move with the ocean currents. Although a 900-pound fish is enormous, for this species it is just a baby. The typical adult size of a sunfish is 2,200 lbs. However, the largest sunfish documented weighed in at 4,927 pounds and was 10 feet long with a large 14-foot measurement from dorsal to anal fin (top and bottom fins).
Flash memory is inexpensive. The attackers properly changing the firmware might hack any device that uses the compromised SD card (e.g. a mobile device, Wi-Fi equipped camera); the flash memory will show up to be running normally while hacking the hosting equipment.
The hardware hacker Bunnie Huang presented during the Chaos Computer Club Congress how to exploit SD cards micro controlled for malicious purposes.
Just how are you able to exploit SD Card, USB stick with other mobile devices for hacking? Another interesting hack ended being presented at the Chaos Computer Congress (30C3), in Hamburg, Germany. Recently, a post on a hack against ATMs by means of infected USB sticks published.

The researchers explained how exactly to hack the microcontroller inside every SD as well as microSD flash cards to understand someone in the middle attack.
SD cards have powerful micro controllers, which are exploitable by hackers to ensure they are insecure.
The hacker, Bunnie Huang described the process to get it done and published the topic. To reduce SD cards price and increase their storage capability, engineers need to think about a form of internal entropy that would affect data stability on every Flash drive.
In 2006, the AIDS incident was a quarter-century old. The disease was first discovered in homosexual men from Manhattan. The epidemic did not begin in Africa. The first AIDS case was uncovered in Manhattan in 1979. The AIDS epidemic in Africa did not start until the autumn of 1982 at the earliest. Before discovering the man-made theory of AIDS, it is worth watching a small but extremely vocal team who considers the cause of AIDS is still unidentified, the AIDS blood test is worthless, and that HIV is a harmless virus that is not sexually transmitted.
Formally starting in July 1981 as a strange and critical illness specifically discovered in several number of younger white gay men from New York City and Los Angeles. The disease has already killed 20 million people with 40 million more currently contaminated with the Human Immunodeficiency Virus (HIV), commonly approved as the only cause of AIDS. One million Americans are now contaminated with HIV; and almost 50 percent of the new cases are African-American.

The disease was first discovered in homosexual men from
Manhattan. “Gay cancer,” by means of Kaposi’s sarcoma skin tumors, was the most stunning identifying sign. Drugs, promiscuity, and anal sex were all believed to be a cause in the unmatched decline of the immune system. It was soon obvious the disease was not limited to gays: the strange agent was in the national blood supply, and an incident of AIDS was discovered in
Central Africa.
In April 1984, Robert Gallo of the US National Cancer Institution (NCI) announced his finding of HIV as the cause of AIDS. Thus, Luc Montagnier of the Pasteur Institute in Paris filed a lawsuit claiming he had first discovered the AIDS virus at Pasteur, and that Gallo had stolen the French virus after it was sent to his lab for study.
"One reason we began placing our own satellite navigation was that, first, we don't need to depend on the prospect of being stop because it may occur to the Americans to do, and, second, we wish to rule out wherever the GPS may well be used to spy on the movements of a number of our sensitive shipments or peoples',"
Alexander Vlasov, marketing Director for the Grotek company told the Voice of Russia.
The United States doesn't want GLONASS stations on its territory. Americans are afraid that Russia's GLONASS global satellite navigation system might be used to spy on the US. No official ban has been imposed, but the new requirements that have been suggests now create the placement of ground-based tracking stations next to impossible.

The 2014 defense bill signed by President Barack Obama rules the navigation systems of other countries should not harm the American GPS system by creating it less commercially engaging and obliged to broadcast solely uncodified data.
Despite that unfriendly gesture towards GLONASS, satellite navigation is a sphere where cooperation and teamwork ought to prevail, Alexei Smyatskikh, General Director of the Space Team holding, told the Voice of Russia.
"There aren't any controls on GPS signal reception or use in Russia or anyplace in the world. We have always been open to cooperation. All specialists have always said and continue saying that customers will benefit much more by using each systems - the GLONASS-GPS combination - than by using only one," Smyatskikh said.
The Russian side applied for permission to create GLONASS tracking stations on US soil in May 2012.
The US State Department was about to grant it but faced strong criticism from Congress and the Pentagon amid fears that Russia may potentially use those stations for spying on the US, so a clause in the defense bill requiring that foreign satellite navigation systems broadcast only uncodified data.
The problem is, however, the American side too can use its GPS system for military works. So, should Russia respond?





























.jpg)